HIPAA & Cyber Security Protection for Healthcare (i.e. Dental, Medical, Pharmacies)
We secure your practice, simplify compliance, and protect patient data - so you can focus on care.

With reimbursements shrinking, your practice can’t afford downtime, breaches, or audit fines.
Whether you're running hybrid telehealth or expanding to new locations, we help ensure you're secure, compliant, and always-on—without the stress of managing it yourself.
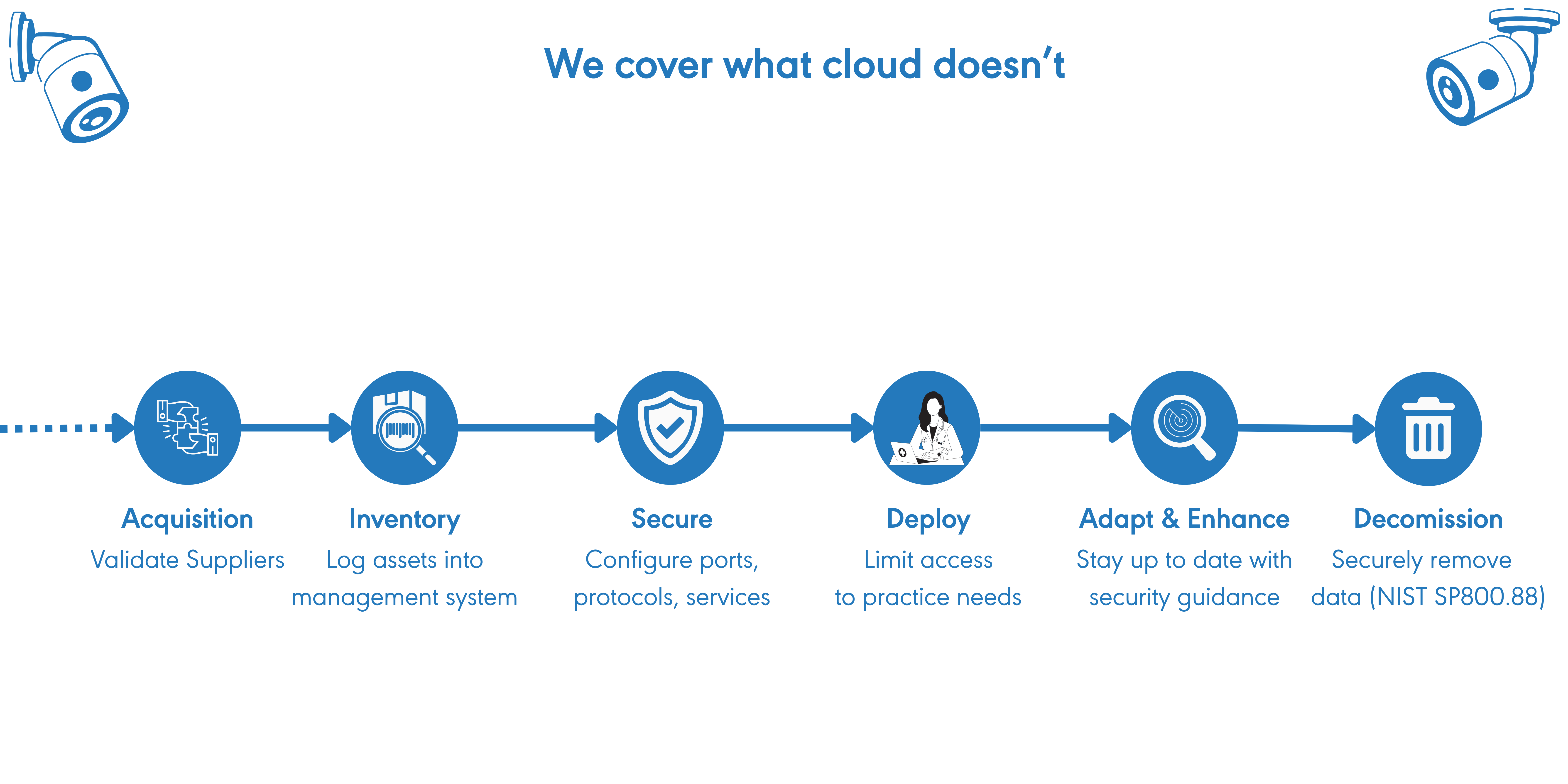
When Tech Isn’t Their Job—But They’re Doing It Anyway
Having someone “good with computers” isn’t the same as defending against real-world threats. From physical access to cloud leaks, ransomware, and device misuse—HIPAA requires more. We fill those gaps, fast.
Privacy and Pressure
Whether on-premise, in the cloud, or at home, your patients expect privacy, and so do you. But keeping data protected gets harder as visit volume rises and systems are pushed to the limit. We help you stay compliant, secure, and operational—no matter how fast things move.
Hybrid & Remote Support
Whether staff are working from home or providers are doing virtual visits, we help make sure remote access is secure, compliant, and reliable—no matter where care happens.
Cloud EMR ≠ HIPAA Compliance.
Even if you use a cloud system, you are still responsible for staff training, policies, and risk assessments.
We make compliance simple — while keeping your IT secure.
HIPAA (Health Insurance Portability and Accountability Act) is a U.S. law that establishes national standards for the protection of health information. It requires healthcare providers, insurers, and their business associates to implement safeguards to ensure the confidentiality, integrity, and availability of protected health information (PHI).
HITECH (Health Information Technology for Economic and Clinical Health Act) is a U.S. law that promotes the adoption of health information technology, particularly electronic health records (EHRs). It also strengthens the privacy and security protections established under HIPAA, especially regarding data breaches and patient notification.
The NY SHIELD Act (Stop Hacks and Improve Electronic Data Security) is a New York state law that enhances data security requirements for businesses. It requires organizations to implement reasonable safeguards to protect private information and mandates notification of data breaches affecting New York residents.
PCI (Payment Card Industry) compliance refers to a set of security standards designed to ensure that organizations that handle credit card information maintain a secure environment. It is essential for businesses that process, store, or transmit credit card data to protect against data breaches and fraud.
HIPAA sets the foundation for protecting patient data, while HITECH builds on it by enhancing breach notification requirements and promoting data encryption. HITECH also incentivizes healthcare providers to adopt electronic health records (EHRs).
BAA & Secure Hosting
We sign Business Associate Agreements (BAA) with all covered entities and host our infrastructure on HIPAA-compliant platforms. Your data remains encrypted in transit and at rest, with strict access logging, endpoint control, and disaster recovery protocols in place. We track access logs, encrypt data, and perform regular internal audits.
Compliance Packages
Basic
Small practices (<8 users, up to 2 sites)
✔ Core IT support
✔ HIPAA Risk Assessment
✔ Essential policies
✔ Staff training (HIPAA, OSHA, FWA)
Growth
Most practices (6–20 users, up to 5 sites)
✔ Everything in Basic
✔ HR & custom policies
✔ Compliance portal
✔ Expanded training library (Cybersecurity, DEI, Harassment)
Advanced
Larger practices (20–25+ users, up to 10 sites)
✔ Everything in Growth
✔ Full Training Library (Healthcare and Clinical Workforce)
Compliance Add-On Packages
A basic HIPAA Risk Assessment is already included.
Incident Management
Hotline integration & Investigation ($79/mo)
3rd Party Risk
Vendor/Contract/BAA Management ($79/mo)
Advanced HIPAA Risk Assessment
Breach notification, Data security, Privacy & Physical safeguards programs EEOC & SAFER Assessments ($379)
Active Monitoring & Ongoing Support
You have patients. If you need help, we will be there for you. We want you to be able to focus on patients while we deal with the nuances of running an office. Whether it's on-site or remote support, do not worry.
We have you covered from user activity to physical system components to software activity to network and firewall logs.
Asset and Data Sanitation & Destruction
If we need to come to sanitize and destroy equipment on site, it can be combined with the cleaning and quarterly checkup. We have secured offline erasers, duplicators, and portable crushers to meet NIST requirements (As per NIST SP 800-88 "Guidelines for Media Sanitization").
What to expect
Let's Get to Know Your Practice
Understanding your unique environment helps us tailor your compliance and IT roadmap.
Business Operations
We'll define your working hours, key team roles, and any remote work or hybrid setups so we can structure secure access properly.
Service Providers & Access
We’ll identify your Internet, phone, and fax vendors—and understand how and when staff use systems to help restrict unauthorized use.
Data & Security Practices
From network architecture to data flow and inventory, we’ll map where sensitive data lives and how it moves—laying the groundwork for security policies.
Resilience & Compliance Gaps
We'll check for a disaster recovery plan, retention rules, identity lifecycle procedures, and readiness to respond to an incident—all part of HIPAA & HITECH.
How We've Established Trust
Real-world incidents where we protected data, detected threats, and helped our clients stay secure.
Guest Device on Provider Wi-Fi
A provider allowed a visitor onto their home network. Our system flagged the connection attempting to attack, isolated the risk, and Provider was notified in under 30 minutes—no data compromised.
Unauthorized USB Device
Someone inserted a tiny USB dongle into a remote clinic PC. Our system auto-isolated the computer. We dispatched an onsite team to review the device and confirmed it was a malicious USB tool. No data loss occurred, and controls were tightened.
Skimmer in Fake ATM Panel
We helped identify a disguised card skimmer with hidden storage. Our team reverse-engineered how it worked and provided forensic support to investigators.
Cut your audit risk. Stop ransomware. Keep systems up 24/7—so you can care for patients without tech drama.
In today's fast-evolving digital landscape, medical and dental offices face increasing challenges in compliance, security, and efficiency. With stringent HIPAA regulations, cybersecurity threats, and the complexities of modern patient care, your practice needs more than just an IT provider—you need a partner who understands healthcare inside and out.
That's where we come in. Expanding from our expertise in precision technology, 3D printing, and front-end, and back-end development, we now offer specialized Healthcare IT solutions across New York City, Rockland County, Westchester County, Bergen County, Passaic County, and Orange County.
For all areas outside of our service, we would need some help from your staff for bi-annual audits and installs (we can remotely configure or test and ship out preconfigured units).
Our mission is simple
Empower your practice with reliable, secure, and fully compliant IT infrastructure so you can focus on what matters most—your patients.
Frequently Asked Questions
Get Started Today!
Schedule a consultation below
Leave a message in the chat
Call us at
Email us at ITSupport@SnoLabs.com
